
Web App and Penetration Testing
Web Application Penetration Testing is done by simulating unauthorized attacks internally or externally to get access to sensitive data. A web penetration helps end user find out the possibility for a hacker to access the data from the internet, find about the security of their email servers and also get to know how secure the web hosting site and server are
Fill the form & get free demo session
Contact Us
Web Application Penetration Testing
Web Application Penetration Testing Training focuses on preparing students for the real world of Web App Pen Testing through extensive lab exercises and thought-provoking lectures led by an expert instructor. We review of the entire body of knowledge as it pertains to web application pen testing through a high-energy seminar approach. Sysap offers Web Application Penetration Testing program to train and prepare IT Security Professionals.
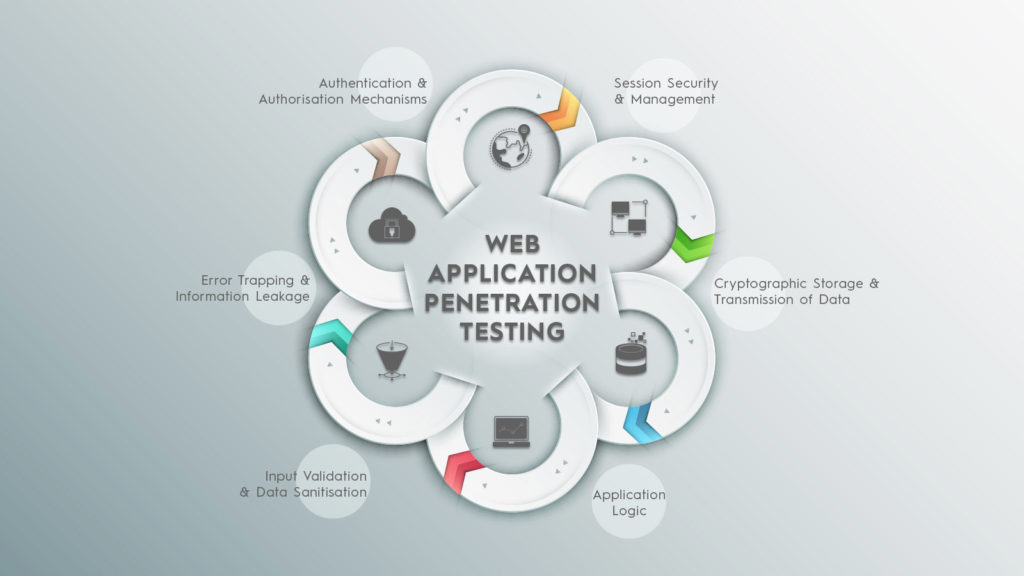
Course Highlights
- Learn the Secrets of Web App Pen Testing in a totally hands-on classroom environment
- Learn how to exploit and defend real-world web apps – not just silly sample code
- Complete the 83 Step "Web App Pen Test Methodology", and bring a copy back to work with you
- Understand how to find Vulnerabilities in Source Code
- Take home a fully featured Web App Pen Test Toolkit
- Learn how perform OWASP Top 10 Assessments – for PCI DSS compliance
Intensive Hands-On Training
The Web Application Penetration Testing course from Sysap is a totally hands-on learning experience. From the first day to the last day, you will learn the ins and outs of Web App Pen Testing by attending thought-provoking lectures led by an expert instructor. Every lecture is directly followed up by a comprehensive lab exercise (we also set up and provide lab workstations so you don’t waste valuable class time installing tools and apps). Typical lab exercises consist of a real-world app that demonstrates a vulnerability commonly found in a web app.
You learn how to assess the application much as a black hat hacker would, and then exploit the app so that you can demonstrate the true risk of the vulnerability to the application owner. This can involve taking control of the application itself, downloading data the application stores, or potentially using the app as a launching pad to attack unsuspecting visitors with a malicious script. Finally, the lab will follow up with remediation steps so that the application owner can properly close down the security hole for good.
COURSE CONTENTS
-
Web Application (In)security
-
Core Defense Mechanisms – OWASP Top 10
-
Cross-Site Scripting (XSS)
-
Broken Authentication and Session Management
-
Insecure Direct Object References
-
Cross-Site Request Forgery (CSRF)
-
Insufficient Transport Layer Protection
-
Unvalidated Redirects and Forwards
-
Cross-Site Request Forgery (CSRF)
-
Bypassing Client-Side Controls
-
Transmitting Data via the Client
-
Encoding Schemes, URL Encoding, Unicode Encoding
-
Decompiling Java Bytecode
-
Coping with Bytecode Obfuscation
-
Hacking ASP.NET ViewState
-
Manipulating Exported Functions
-
Attacking Authentication
-
Reverse Engineering ActiveX
-
Exploiting Vulnerable Transmission of Credentials
-
Attacking Password Change & Forgotten Password Functionality
-
Exploiting Verbose Failure Messages
-
Prevent Misuse of the Account Recovery Function
-
Attacking Session Management
-
Predictable Usernames & Initial Passwords
-
Common Vulnerabilities
-
Targeting Identifier-Based Functions
-
Attacking Access Controls
-
Injecting into Interpreted Languages
-
Exploiting ODBC Error Messages (MS-SQL Only)
-
Securing Access Controls
-
Extracting Arbitrary Data
-
Parameterized Queries
-
Enumerating Table and Column Names
-
File Inclusion Vulnerabilities
-
Preventing SOAP Injection
-
Finding Dynamic Execution Vulnerabilities
-
Injecting into LDAP
-
Storing XSS in Uploaded Files
-
SMTP Command Injection
-
Chaining XSS and Other Attacks
-
HTTP Response Splitting
-
Real-World XSS Attacks
-
Exploiting Information Disclosure Vulnerabilities
-
Exploiting Error Messages
-
Exploiting XSRF Flaws
-
Heap Overflows
-
“Off-by-One” Vulnerabilities
-
Buffer Overflow Vulnerabilities
-
Attacking Tiered Architectures
-
Exploiting Trust Relationships between Tiers
-
Attacking & Assessing Application Architectures
-
Attacking Other Tiers
-
Source Code Auditing
-
Subverting Other Tiers
